thick client pen testing|thick client pentest checklist : wholesaler Penetration testing of thick clients follows a systematic approach to ensure comprehensive assessments. The process can be divided into three main phases: pre-testing preparations, execution of penetration testing, and post . Page couldn't load • Instagram. Something went wrong. There's an issue and the page could not be loaded. Reload page. 3,123 Followers, 2 Following, 71 Posts - See Instagram .
{plog:ftitle_list}
Top Tags. The World Famous Thumbzilla.com, Porn hub is t.
How to test thick client applications? 👨💻. Thick Client Pentest is complicated as compared to /API Pentest in my opinion. In Thick Client, there are two types (i) Proxy-based Thick clients. (ii) Non-Proxy based thick . Thick client penetration testing is the systematic evaluation of security measures in desktop applications to discover and address vulnerabilities, enhancing the overall security posture of the software and .
Penetration testing of thick clients follows a systematic approach to ensure comprehensive assessments. The process can be divided into three main phases: pre-testing preparations, execution of penetration testing, and post . Thick client penetration testing is an assessment process aimed at evaluating the security of these desktop applications by identifying vulnerabilities, testing authentication mechanisms, assessing data encryption, .
Welcome to the Thick Client Penetration Testing Repository! This repository aims to familiarize you with Thick Client Application security concepts, providing a comprehensive guide and .In this article, we have set up a lab to practice thick client application penetration testing and then we discussed various information gathering techniques. In the next article, we will discuss .
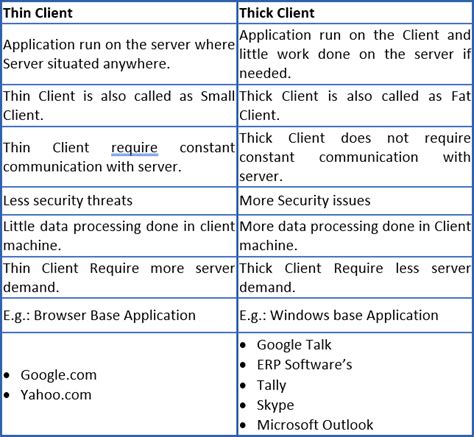
What Is Thick Client Penetration Testing? A thick client, also known as a fat client, is a client application that can provide rich functionality, independent of the server in a . Thick client penetration testing is a specialized practice that focuses on identifying and addressing security flaws within these locally executed applications. This.
There are a few common challenges when it comes to thick client testing. The first challenge is setting up the correct environment. You have to do this every time. Every test can require a different type of environment. So, for .
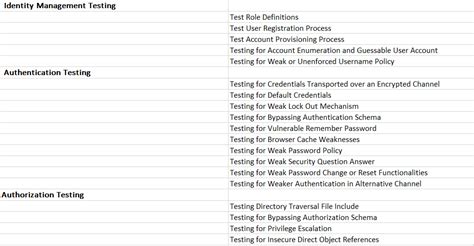
Test For File And Content Manipulation. Try framework backdooring; Try DLL preloading; Perform Race condition check; Test for Files and content replacement; Test for Client-side protection bypass using reverse . What is Thick Client Penetration Testing, and how is it done? Thick Client Penetration Testing checklist and complete guide.Here is a comprehensive 2022 guide to Thick Client Application Security & .When it comes to thick client penetration testing, there are several tools that are commonly used by security professionals. One such tool is Burp Suite, which is a powerful platform for performing security testing of web applications.It provides functionalities like intercepting and modifying network traffic, performing code analysis, and executing exploits.Testing thick client applications for security vulnerabilities requires expert manual penetration testing skills and a thoughtful, methodical approach. NetSPI’s thick client app penetration testing uses multi-vector cybersecurity testing to identify design and configuration weaknesses.
Thick Client Penetration Testing (a.k.a. Thick Client Pentest, Thick Client VAPT, Thick Client Pen Testing) identifies exploitable vulnerabilities on both the local and server-side. The attack surface is larger and requires a different approach from web application penetration testing. Such process often requires specialized tools and custom .
wood moisture meter rental
web penetration testing checklist
If a thick client application has a built-in feature to set up a proxy server, then it is known as a proxy-aware Thick client. Testing these types of thick clients is easy and straightforward due . As a result, both the request as well as response modifications play a key role in testing the thick client for vulnerabilities. Sample Exploit 1. . GADI007 is an Information Security Professional with experience in network and application penetration testing. He is currently a security researcher at Infosec Institute and works for a .
10.5. Test Number of Times a Function Can Be Used Limits 10.6. Testing for the Circumvention of Work Flows 10.7. Test Defenses Against Application Misuse 10.8. Test Upload of Unexpected File Types 10.9. Test Upload of Malicious Files 10.10. Test Payment functionality 11.Client-side Testing 11.Client-side Testing 11.1. Why thick client penetration testing? Thick client applications are not new having been in existence for a long time, however if given to perform a pentest on thick clients, it is not as simple as a Application Pentest. Thick clients are majorly used across organizations for their internal operations. Launch CFF Explorer tool and load the DVTA file into it. DVTA is vulnerable thick client application. As you can see in the below figure, DVTA.exe will appear in the list of running processes.
Thick client penetration testing is a specialized practice that focuses on identifying and addressing security flaws within these locally executed applications. This blog post aims to delve into .
BreachLock thick client application penetration testing assesses applications that operate on users devices and communicate with a server or backend system. During thick client penetration testing, we identify security weaknesses not only in the applications themselves but also their interactions with networks and other aspects of their security. Testing thick client applications, for example, requires patience and a systematic approach, and simple automated assessment scanning does not suffice. . and eWPTXv2. He has experience penetration testing with mobile apps, web applications, networks, cloud configurations, and thick-client apps. Bash, Python, Go, and PowerShell are his . Information gathering is a critical initial phase in thick client application penetration testing, focused on collecting detailed data about the application’s architecture, components, and interactions with servers. This phase aims to identify communication protocols and potential entry points for exploitation.
For thick client penetration testing, there are two key methods: Black-Box Testing: It is the testing approach where the testers initiate the test without any prior knowledge about the app’s configurations. They carry out the .Enrol on a thick client penetration testing course to get an insight into the thick client penetration testing methodology. Learn thick client penetration testing tools, thick client enumeration, thick client vulnerabilities, and exploitation.
Key Methodologies in Pen-Testing Thick Client Apps: Static Analysis and Code Review: For instance, a thick client application designed for inventory management undergoes thorough code reviews. The .
Thick Client Penetration Testing aims to assess and ensure the secure deployment of thick client or native applications by simulating real-world attacks and analysing potential weaknesses. This comprehensive testing process helps uncover critical vulnerabilities that could be exploited by malicious actors, ensuring that the application’s . Thick client penetration testing (TCPT) is a type of security assessment that focuses on identifying and exploiting vulnerabilities in thick client applications. Thick clients are software applications that are installed on a user’s computer and run locally. They are often used for tasks such as accessing corporate networks, managing .
thick client pentest checklist
The thick clients we come across most often at NetSPI are written in C# and a bit long in the tooth. In these applications, there are two main GUI platforms: . Explore how modern penetration testing tools uncover vulnerabilities in mainframe applications, highlighting the need for methodical techniques and regular testing to protect these .SecureLayer7 begins its thick client application pen testing service by understanding each application's intricacies and functionality. The methodology involves reverse engineering to identify hard-coded secrets, authentication weaknesses, insecure data handling, and potential client-side exploits like buffer overflows and injection attacks . Thick client (Desktop) application penetration testing is the process of evaluating the security of a thick client application by simulating attacks to identify vulnerabilities. A thick client application, also known as a fat client , is a software program that runs on a local machine and communicates with a server or a database to perform its .
Here’s a comprehensive methodology for thick client penetration testing: Thick Client Penetration Testing Methodology 1. Pre-Engagement Preparation.Thick client penetration testing provides a crucial layer of security assessment for applications installed on user machines, addressing vulnerabilities specific to desktop environments. By identifying and mitigating weaknesses such as insecure data storage, inadequate authentication mechanisms, and potential code tampering, your organisation .Tip from Udemy course Mastering thick client application penetration testing by Srinivas. We can go in the folder of the app we are analyzing and open the command prompt from there. We can then run our app and put the output of the execution of our app in a log file using the following command: ourapp.exe > ourapp-logs.txtThick Client penetration testing is an ethical hacking security assessment carried out to uncover vulnerabilities in the thick client software application, network traffic, and backend interface and prioritize remediation efforts to mitigate cyber risks. Tell us. about your scope. Name
wood moisture meter reviews uk

web23 de fev. de 2024 · At the end of 2021, the Flash version of Tanki Online was discontinued, leaving HTML5 as the only playable version. Gameplay. The gameplay of Tanki Online has some parallels with the 1985 game Battle City. Unlike Battle City, the basis of the gameplay of Tanki Online is a player versus player system. Players compete with each other: every .
thick client pen testing|thick client pentest checklist